Improve Your Data Strategy with Universal Cloud Storage Service Solutions
Improve Your Data Strategy with Universal Cloud Storage Service Solutions
Blog Article
Taking Full Advantage Of Data Safety And Security: Tips for Securing Your Details With Universal Cloud Storage Space Solutions
By executing durable data protection steps, such as security, multi-factor authentication, routine back-ups, gain access to controls, and checking procedures, customers can significantly improve the security of their information saved in the cloud. These strategies not only fortify the integrity of details yet also infuse a feeling of self-confidence in turning over critical data to shadow systems.
Value of Information Security
Information encryption serves as a foundational pillar in protecting sensitive info kept within global cloud storage space solutions. By inscribing information as if just accredited events can access it, security plays a critical duty in shielding confidential details from unauthorized access or cyber risks. In the realm of cloud computer, where information is usually sent and saved throughout different networks and servers, the need for durable security devices is extremely important.
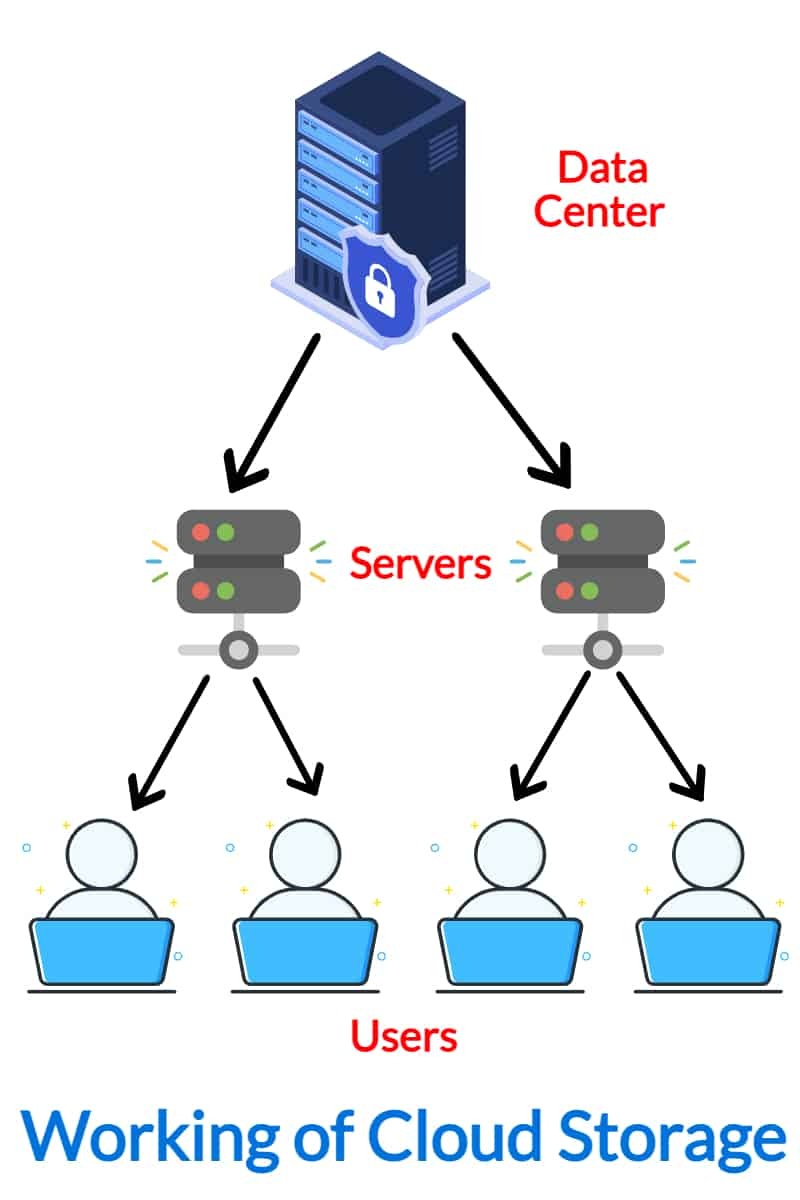
Additionally, compliance laws such as the GDPR and HIPAA need information file encryption as a way of shielding sensitive details. Failure to comply with these requirements can lead to extreme consequences, making data file encryption not simply a safety measure however a legal requirement in today's electronic landscape.

Multi-Factor Verification Approaches
In improving protection measures for universal cloud storage space solutions, the implementation of robust multi-factor verification approaches is vital. Multi-factor verification (MFA) includes an extra layer of safety and security by needing customers to provide multiple types of confirmation prior to accessing their accounts, significantly reducing the danger of unauthorized access. Typical factors used in MFA consist of something the user recognizes (like a password), something the individual has (such as a smart device for receiving verification codes), and something the user is (biometric information like finger prints or face acknowledgment) By combining these elements, MFA makes it much harder for harmful actors to breach accounts, also if one aspect is endangered.
Organizations needs to likewise inform their customers on the importance of MFA and offer clear directions on exactly how to establish up and utilize it securely. By applying strong MFA approaches, companies can considerably strengthen the safety of their data kept in global cloud services.
Normal Data Back-ups and Updates
Given the essential role of guarding data honesty in universal cloud storage solutions through durable multi-factor verification techniques, the following important facet to address is ensuring routine information backups and updates. Routine information backups are crucial in alleviating the threat of data loss because of numerous elements such as system failings, cyberattacks, or accidental deletions. By backing up data constantly, organizations can bring back info to a previous state in case of unexpected occasions, thereby preserving organization continuity and avoiding substantial disturbances.
In addition, remaining up to day with software application updates and safety and security patches is equally essential in boosting information safety within cloud storage services. In significance, routine data backups and updates play a pivotal duty in strengthening data security actions and guarding important info kept in global cloud storage services.
Executing Strong Gain Access To Controls
To develop a durable security structure in universal cloud storage solutions, it is necessary to carry out strict access controls that manage individual permissions successfully. Access controls are essential in protecting against unauthorized access to sensitive data kept in the cloud. By executing solid gain access to controls, companies can guarantee that just licensed personnel have the needed permissions to watch, edit, or remove data. This aids reduce the threat of data violations and unauthorized information manipulation.
One reliable means to apply access controls is by utilizing role-based access control (RBAC) RBAC designates details functions to individuals, providing them gain access to civil liberties based on their role within the company. This technique makes sure that users only have accessibility to the information and functionalities needed to execute their work responsibilities. Furthermore, carrying out multi-factor verification (MFA) adds an extra layer of safety by calling for customers to provide multiple types of verification before accessing delicate information.
Surveillance and Bookkeeping Information Gain Access To
Building upon the structure of solid accessibility controls, efficient tracking and auditing of information access is vital in maintaining data protection stability within global linkdaddy universal cloud storage cloud storage services. Surveillance data gain access to entails real-time tracking of who is accessing the information, when they are accessing it, and from where. Bookkeeping data gain access to entails reviewing logs and documents of information access over a particular duration to make certain compliance with safety plans and regulations.
Conclusion
Finally, safeguarding data with universal cloud storage solutions is critical for protecting sensitive info. By applying information encryption, multi-factor authentication, routine backups, solid gain access to controls, and checking data access, organizations can reduce the danger of information violations and unapproved accessibility. It is necessary to prioritize data safety and security determines to guarantee the privacy, stability, and accessibility of data in today's digital age.
Report this page